What exactly is a DDoS attack? In simple terms, a cyberattack overwhelms a target by flooding it with traffic from multiple distributed machines, such as computers or smart devices located in various locations. The aim is to disrupt or completely halt the targeted services. DDoS attacks are the most prevalent form of denial-of-service attacks.
To effectively combat a DDoS attack and reinforce your defenses, it’s essential to employ technical safeguards, such as utilizing DDoS protection services, and develop robust business strategies to anticipate potential attacks.
Understanding the mechanics behind a DDoS attack is crucial in implementing preventive measures. In the early days of the internet, when dial-up connections were the norm, denial-of-service attacks emerged. Dial-up connections were slow, with a maximum speed of 56,000 bits per second, significantly slower than today’s broadband connections. Loading a single page on a modern website would take over a minute on average.
Attackers with access to faster internet speeds, like those available to businesses and universities, would target a specific entity and flood it with massive data, overwhelming its capacity to handle additional connections. The key to a successful attack was having a faster internet connection than the target, exhausting its available bandwidth.
While this type of cyberattack does not involve data theft or permanent system damage, it severely impacts websites, rendering them incapable of serving their users due to the flood of illegitimate requests.
Recently, this type of denial-of-service flood attack has become less prevalent due to the difficulty of having a single computer with enough bandwidth to bring down a website single-handedly. However, attackers have adapted and devised alternative methods of denial-of-service attacks to circumvent this limitation.
As the threat landscape grows, staying vigilant and exploring comprehensive strategies to safeguard your systems against DDoS attacks is crucial. By staying informed and implementing robust preventive measures, you can ensure the uninterrupted availability of your services while protecting your users from the disruptive effects of such attacks.
Understanding the Types of DDoS Attacks
In today’s digital landscape, it’s increasingly common for cybercriminals to deploy multiple distributed denial-of-service (DDoS) attacks in a single onslaught. As cybersecurity experts explain, the objective is to overwhelm the network by bombarding it with various elements. These attacks can be broadly categorized into four primary types.
Firstly, we have the Slowloris attack, which operates differently from traditional DDoS attacks. Instead of inundating the target server with excessive data, Slowloris prolongs each request indefinitely. By exploiting the communication mechanism between web servers and clients, this method monopolizes all connections to the server, effectively controlling all traffic. It’s worth noting that Slowloris attacks are particularly potent against servers that struggle to manage numerous simultaneous connections.
Secondly, there are application layer attacks. These resemble traditional denial-of-service flood attacks but operate on a larger scale. Bots flood the target with a deluge of traffic, causing congestion and obstructing access for legitimate users. The attackers typically concentrate on time-intensive endpoints that demand large database queries or generate substantial files. While these endpoints don’t require significant resources from the attacker, they are bandwidth-intensive for the target, rapidly exhausting its available resources.
Third is the SYN flood attack, which targets the transmission control protocol (TCP) and manipulates the standard handshake process to establish connections. In this attack, the assailant sends only the initial part of the handshake to the target server. The server responds with the second part, but the attacker deliberately refrains from sending the final acknowledgment. This leaves the server waiting and unable to use that connection to respond to extra requests. This technique significantly amplifies the impact on the target.
Lastly, we have amplification attacks. These leverage various internet protocols to magnify the size of each request sent by the attacker. An example is the DNS amplification attack, which takes advantage of the DNS protocol. By spoofing the request’s source to make it appear as if it originated from the target, the attacker tricks the DNS server into sending a substantial amount of data to the target.
The amplification effect stems from the minimal bandwidth needed for the attacker to send the request compared to the bandwidth required for the target to receive the response. Furthermore, the attacker can send requests to multiple DNS servers, exacerbating the impact. As with any distributed attack, the scale of damage escalates with the number of bots in the botnet executing the attack.
How to Prevent a DDoS Attack
To shield their systems from falling prey to a DDoS attack, organizations can adopt the following proactive measures:
- Scale Up Connection Servers: DDoS attacks seize network connections and bandwidth, depriving legitimate users of necessary resources. By promptly scaling up servers to accommodate increased connections and bandwidth, the impact of such attacks can be lessened, although this may entail additional costs. Cloud-based hosting providers often offer a convenient solution for this purpose.
- Protect Critical Endpoints: A prudent strategy is safeguarding resource-intensive endpoints from bots. Organizations can accomplish this by positioning endpoints that carry out tasks such as database queries or large file downloads behind protective measures like login pages. Employing widespread security measures, such as CAPTCHA tests, which require users to decipher distorted words or images, can also aid in protecting resource-demanding endpoints from bots.
- Adopt a Modular Website Architecture: The architectural design of websites plays a pivotal role in repelling DDoS attacks. Instead of depending on an interdependent monolithic structure, coding a website as interconnected modules allows unaffected sections to remain operational even if an attack targets one part.
By adopting these proactive measures, organizations can strengthen their defenses against DDoS attacks and ensure consistent service delivery.
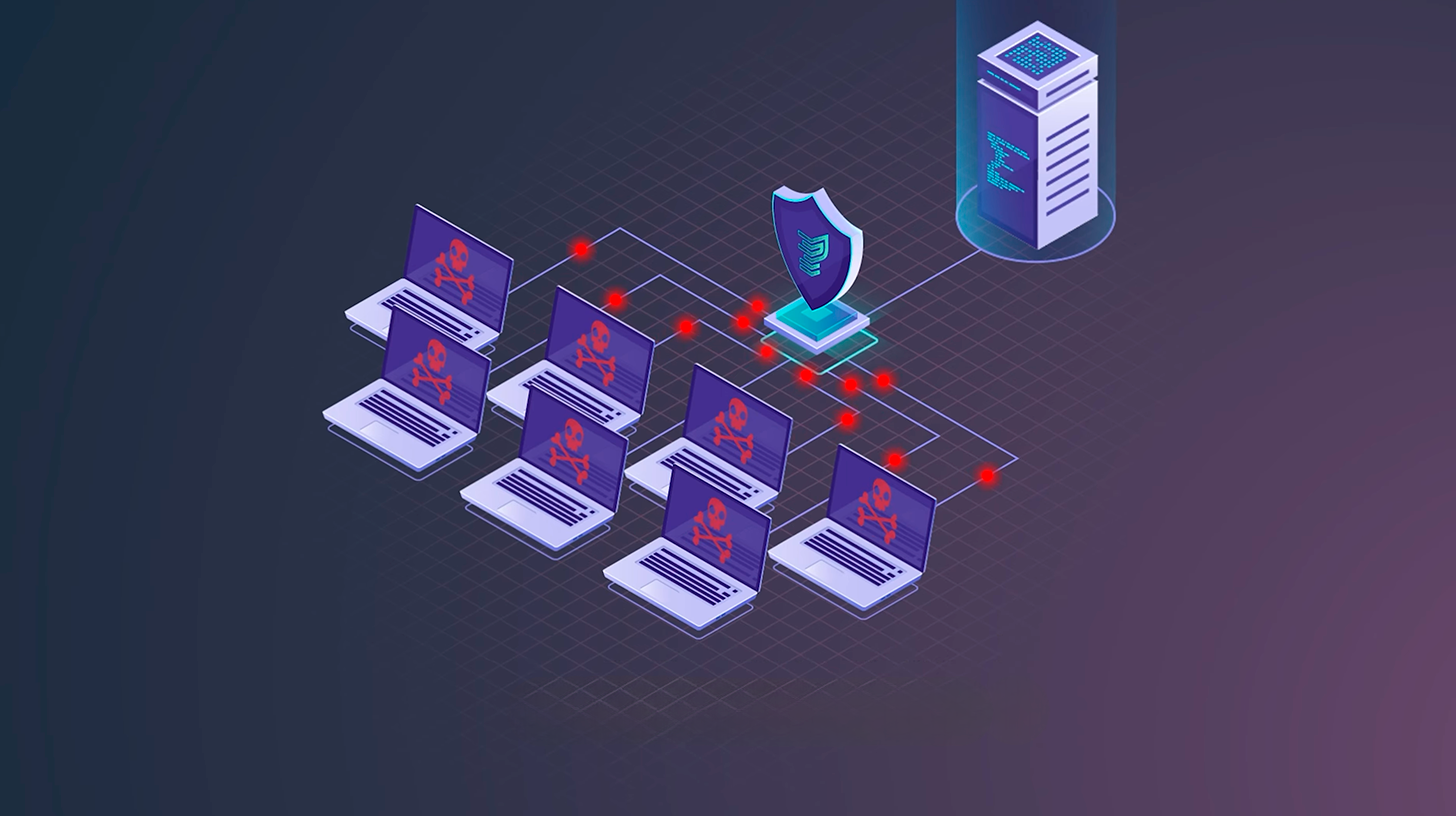
How to Determine and Stop a DDoS Attack
The impact of a DDoS attack on network traffic can serve as a cue to pinpoint the timing and nature of the attack. For users trying to access the targeted website, the page might load poorly or experience significant delays before eventually timing out due to an overwhelming flood of requests.
To detect and counteract DDoS attacks, keep an eye out for multiple connection requests from specific IP addresses within a brief time frame. Also, stay vigilant for abnormal surges in website traffic, unusually sluggish site performance, and significant site outages. DDoS detection software can automate scanning traffic and alert you to suspicious activities.
Once unusual user traffic is identified, refer to system log files to determine the source of the DDoS traffic. From this point, you can apply various tactics to mitigate the attack. One strategy is to block the attacker’s traffic by implementing IP address filtering, which restricts service access from specific IP addresses.
Alternatively, you could employ geo-blocking, which denies access from entire geographical regions. IP filtering is most effective for blocking known and specific traffic sources, while geo-blocking is useful for preventing traffic from unidentified locations.
If blocking traffic proves to be unfeasible, consider redirecting legitimate traffic to a new IP address and altering the Domain Name System (DNS) to obscure targets from public view, making them less susceptible to attacks. Internet service providers can also be enlisted to help reroute DDoS traffic. Although this solution is temporary, traffic migration can halt small-scale DDoS attacks and provide additional time to implement other defense measures.

In extreme cases, as a last-ditch effort to halt DDoS attacks, it may be necessary to shut down the targeted services entirely. While this step will stop the attacker’s traffic, it will also disrupt legitimate user traffic, potentially leading to the loss of customers and revenue.
By deploying these strategies, you can enhance your capacity to identify, mitigate, and guard against DDoS attacks.
Recovering from a DDoS Attack
DDoS attacks can have severe repercussions for a company, including damage to its reputation, financial losses, and significant expenses incurred to mitigate the attack. These attacks prevent legitimate users and customers from accessing the targeted site and disrupt normal business operations, resulting in a loss of purchases and ad revenue.
While DDoS attacks cannot directly steal information, attackers often use them as a diversion tactic to draw attention away from concurrent cyberattacks. While the organization is preoccupied with managing the DDoS, the attackers can pursue their primary objectives. Additionally, prolonged DDoS attacks can be leveraged to extort targets, similar to ransomware attacks.
Companies should have a well-defined response plan to prepare for such attacks. It is suggested to draft a company statement for release to the public and establish a cleanup process to address the aftermath of an attack. Regarding immediate response, it is advisable to challenge or block traffic flow from the DDoS source(s) and identify and restrict site access from the offending machines. Engaging a DDoS protection service can facilitate these responses.

Another important factor is estimating the costs associated with a DDoS attack on the company’s specific sites. This estimation can help determine the company’s readiness to allocate resources to resolve an attack. Making a cost-benefit calculation during a crisis is not advised, especially when the attack is causing ongoing revenue loss.
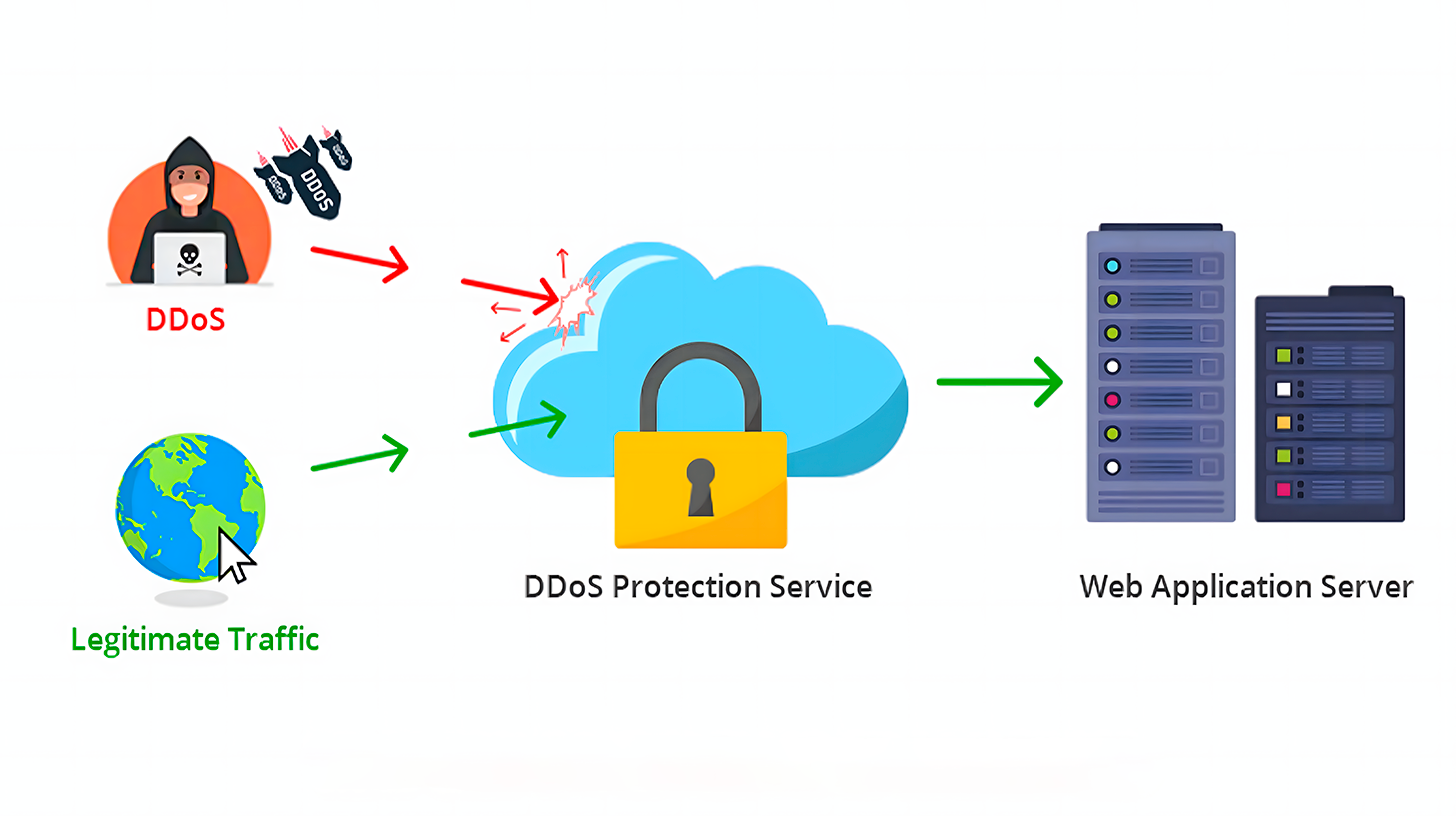
Since DDoS attacks can involve different types, some of which are harder to detect, expecting individual companies to handle them can be challenging. DDoS protection services specialize in mitigating these attacks. They operate a large network of servers worldwide to intercept web traffic on behalf of its customers.
Such services effectively filter out malicious requests by distributing the incoming data across their network and analyzing it for various DDoS attacks. Implementing traffic filtering, where servers only accept traffic from the service’s IP address, reduces risks.
By having well-prepared business strategies and technical protective measures in place, companies can proactively defend against DDoS attacks and ensure their survival.
